One Way Hash Functions and Data Privacy Compliance.
Last Updated: June 27, 2024

This article will discuss how a one way hash function can be used in the context of privacy compliance for regulations like the GDPR. Storing customer’s personal data is an inevitability for scaling businesses in today’s technical world. One way hash functions are a useful tool to store sensitive customer data such as passwords and social security numbers in a blind manner that reduces your risk. We’ll talk about what one way hash functions are, why you should care, and their place in a data privacy compliance context.
The Information Security Challenge
We’ve all seen the headlines about high profile data breaches for sensitive customer data. These breaches are occurring at the highest level companies and information security companies themselves are not immune to targeting by hackers.
Since information security professionals largely find ways to protect against known attacks and hackers are constantly devising new attacks, hackers have the advantage. Because of this, application providers must a) assume that stored data will be breached and b) take appropriate steps to protect the data so that the impacts of a breach are minimized.
Enter the one way hash function.
About One Way Hash Functions
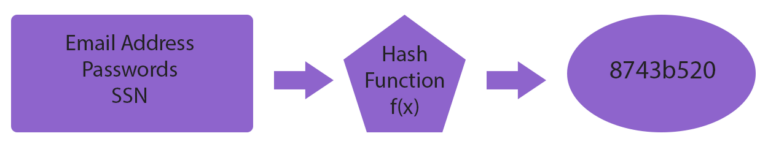
The graphic above illustrates how one way hash functions work. An arbitrary input, such as an email address or password, is provided and run through the hashing function and the result is a fixed-length alphanumeric string of characters.
The provided input will always result in the same fixed length set of characters but it is impossible to determine what the original input was because the encryption algorithm only goes one way.
This gives us a fantastic tool to store customers personal data in such a manner that the application provider has no knowledge of the originally provided input.
For example, lets say a fictitious user is logging in with a password “pass123”.
When the user registers with the password, it is run through a one way hashing function and the resulting hash code “x6y1otB” is generated.
The application provider stores this hash code in their database and has no knowledge of the original password. Yet, when the user attempt to login the next time, the original “pass123” hashes back to “x6y1otB” and we can confirm that they did indeed supply the correct password without ever knowing what it was.
This is a powerful protection in an information security sense because if a hacker was to gain access to the database and steal the stored passwords they will only see the hash codes that were stored and would not be able to decipher what the original password was.
This gives application providers a chance to inform users of a breach, lock out accounts and force password changes while the vulnerability is corrected. It saves a tremendous amount of hassle for the end consumer because their data remains far safer than if the password was stored in plain text and then was subsequently compromised.
If the password was stored in plain text, the hacker would have been able to login to the compromised user’s account and do far more damage.
Emerging Privacy Law
Savvy application providers have been implementing techniques likes this for several reasons.
- Reduces Liability
- Decreases Risk
- Increases Customer Satisfaction
- Decreases the Attractiveness of Attack to Hackers
Data privacy has become a hot topic over recent years and implementing information security is no longer just a tactic employed by top companies for their benefit of their consumers – it’s become a legal requirement.
Data privacy laws such as the GDPR and California Consumer Privacy Act rarely specify the exact solutions required for securing personally identifiable consumer information but they make it clear that efforts to secure customer information must be made, and documented, and must periodically be audited by an appointed data privacy officer within the organization.
As such, the one way hash function has become an important tool in the application providers belt to secure and process personal information.































Leave a Comment